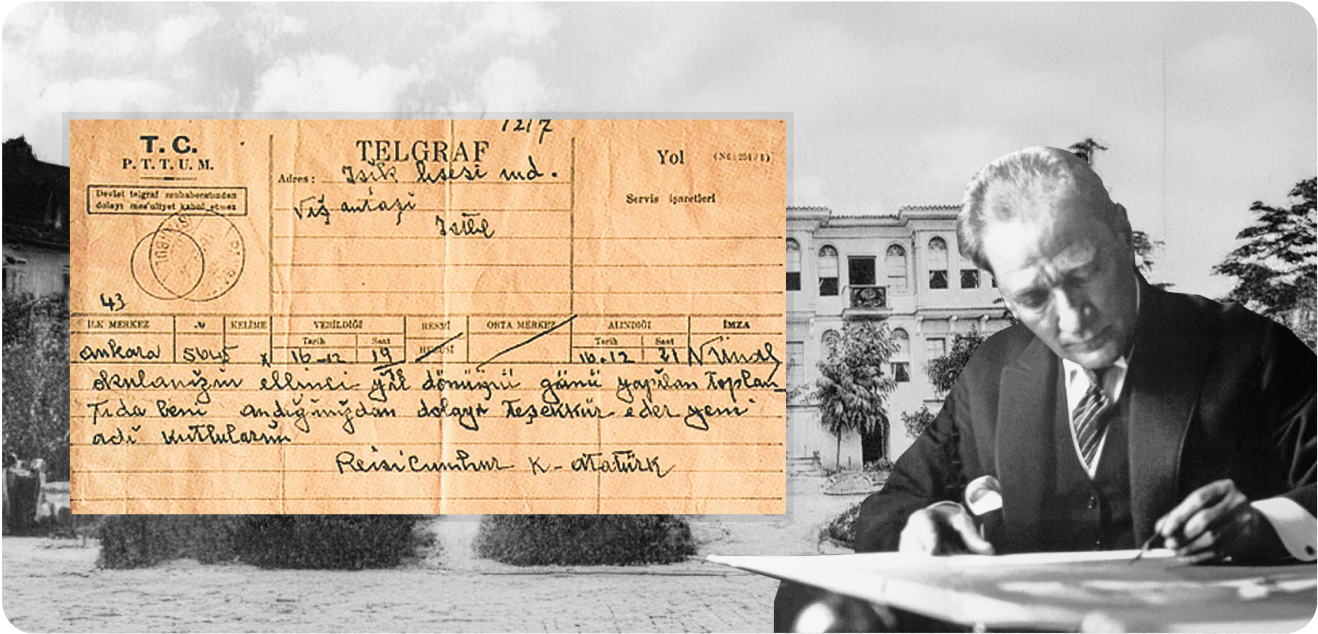
Adını, Büyük Önderimiz
Mustafa Kemal Atatürk’ün
Verdiği Eğitim Kurumu
Feyziye Mektepleri Vakfı Işık Üniversitesi
Işık Üniversitesi’nin Çağdaşlık Hedefleri

Işık Üniversitesi'nde geleceğe hazırlanıyoruz.
Ama Işık Üniversitesi'nde geleceği de hazırlıyoruz.
Prof. Dr. Hasan Bülent KAHRAMAN
FMV Işık Üniversitesi Rektörü
Rakamlarla
Işık Üniversitesi
Haberler
Tüm HaberlerDuyurular
Tüm Duyurular
Rehber Öğretmen Sempozyumu
28 Ocak 2026
Vefat & Başsağlığı
16 Aralık 2025































